Configuring Your Okta SSO Provider
Go Up to Setting Up Single Sign On (SSO)
The following steps are specific for environments using Okta as your SSO provider.
Contents
Activating Okta SSO in the Team Server Configurator
An Administrator must activate Single Sign-On (SSO) in the Team Server Configurator Single Sign-On page before options appear for users to select Okta.
To activate Okta SSO in the Configurator
- In the Configurator, use the available Select SSO Provider drop-down list to choose Okta for enablement.

- The appropriate provider appears.

- The content of the following fields is available when you configure SSO in Okta:
- DomainId. This is the domain ID associated with your Okta provider. This could be a unique identifier provided by the SSO service.
- ClientId. If your ClientId or Client Secret are incorrect or your redirect URL fails, you do not receive any logs. Instead you receive an Okta page with an error message "Invalid request."
- Client Secret. This is the client secret that you receive when you register the application with your Okta provider.
- Authorization. The server that you enter in this field must be the same as provided in the Okta console or you receive an error when attempting to log in.
- Scope. This is the scope of access requested by your application.
- Proxy Server Details. Check this box if you use a proxy server for this machine. Details for the server are automatically populated in the appropriate fields. If you want to change any of these fields, use the Admin user account.

- Once you complete all of the necessary fields, click Test to verify your entries. All responses to these tests are collected in the sso.log file.
- If all of the details are correct, the Update button is enabled. When you click that button, the information is encrypted and saved in a property file, and then Team Server restarts. Once the restart is complete, the Login by SSO button is enabled on the Login page.
Configuring your Okta authentication process
To configure your Okta authentication process
- Create an account at https://www.okta.com/.
- Once in the Okta application, expand the Applications menu, and then click Applications as shown in the following image.
- Click Create App Integration to begin the process of registering the new application.
- In the Create a new app integration window, select OIDC - OpenID Connect for the sign-in method, and then select Web Application as the application type.
- Click Next. The New Web App Integration page appears, as shown in the following image. Note: Please also check grant type "client credentials"
- Complete the appropriate fields in the New Web App Integration page. If at any time you need Okta help, click the adjacent Learn More link. Fields of note include:
- Refresh Token. A refresh token allows you to obtain multiple temporary access tokens without collecting credentials each time a token expires.
- Sign-in redirect URIs. The sign-in redirect URL must use the following format: http://desktop-I5i6j1s/azureSSO/login/oauth2/code/okta or http://desktop-I5i6j1s:8443/azureSSO/login/oauth2/code/okta, where desktop-I5i6j1s and desktop-I5i6j1s:8443 are replaced by your actual domain / port configured for Team Server. Note that if the redirect URL is not properly configured, then the application displays an Okta 404 error. You can find the redirect URL used by the application from the browser string. Copy that string and then use it in your application to prevent any mistyped characters.
- Sign-out redirect URIs. Optional. The sign-out redirect is required when the user is logging out and the SSO provider then redirects the user to a certain page after logging out. The URL must use the following format: http://desktop-I5i6j1s:80/login or http://desktop-I5i6j1s:8443/login, where desktop-I5i6j1s:80 and desktop-I5i6j1s:8443 are replaced by your actual domain / port configured for Team Server. Note that if the Redirect URL is not properly configured, then the application displays an Okta 404 error. You can find the redirect URL used by the application from the browser string. Copy that string and then use it in your application to prevent any mistyped characters.
- Controlled access. Select one of the available options depending on how you want the application integration available to users in your environment. Options include allowing all users, select users, and skip assignment until later.
- Once you complete all of the necessary fields, click Save. The application is now registered on Okta.
- Copy the displayed client ID and client secret information for later use when you must type it into the Configuration in SSO Details page.
- Expand the Security menu, and then click API as shown in the following image. Your available Authorization servers appear in this list or you can create a new auth server.
- If you want to edit an existing server, click the Edit icon for that server or click directly on the server name. You are directed to a server details page where you can make your changes. If you want to create a new server, click Add Authorization Server, and continue with the next step.
- In the Add Authorization Server dialog that appears, complete the available fields.
- Note the information displayed in the Settings tab for the Authorization server you just created, such as the following image. The Metadata URL appears in the following format as this example: https://[DOMAIN]/oauth2/[xxxxxx]/.well-known/oauth-authoriation-server. The [DOMAIN] and [xxxxxx] are what you will add as your Authorization in ER/Studio Team Server. This information also appears in the Issuer URL field in the API page in Okta.
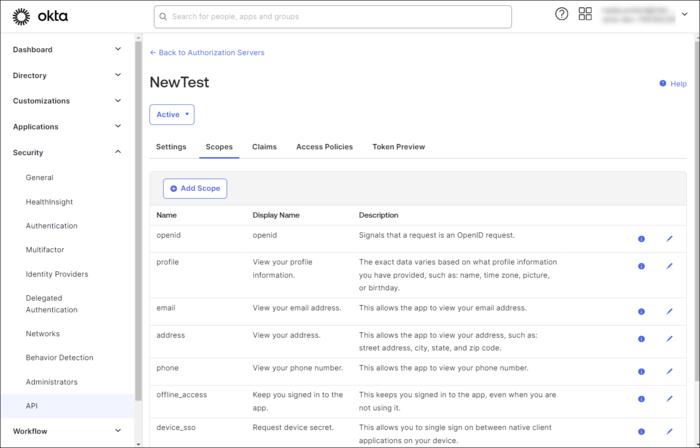
- Click the Scopes tab. This page displays a list of pre-existing scopes. It is recommended to NOT delete any existing scope.
- Click Add Scope. In the Add Scope dialog that appears, complete the available fields before clicking Save. Note the name of the scope as that is used in Team Server.
- Once you save your new Scope, you must add a policy. Click the Access Policies tab. Policies and rules are required for clients to access this Authorization server.
- Click Add Policy.
- Complete the available fields, and then select whether you want this policy to apply to All Clients or only to clients that you enter in the available box.
- Click Create Policy. The system creates your new policy, to which you now must add rules.
- In the policy you just created, click Add rule.
- Complete the available fields to create your new rule. Make sure to use a name that describes what the rule does.
- Once you click Create rule, your new Authorization server and all supporting items are ready for use in the Team Server Configurator when setting up Okta as your SSO provider.
Creating a New user Account in Okta
Use the following steps to create a new user account in Okta.
- Once in the Okta application, expand the Directory menu, and then select People.
- Click Add person, as shown in the following image.
- Complete the appropriate fields to create a new user account, and then click Save. If you are creating multiple users, use Save and Add Another as a shortcut to creating the next user account.