Uses Permissions
Go Up to Project Options Dialog Box
Contents
Project > Options > Uses Permissions
Use this dialog box to specify the permissions that your Android application requires to work. RAD Studio adds the permissions you specify in the AndroidManifest.xml file.
- Caution: Carefully review the list of permissions that are configured for your Android application. You should disable permissions that your application does not need, because:
- Android devices prompt your users to accept every requested permission when they run your application for the first time.
- Application stores such as Google Play may use permissions to filter out applications.
- For example, if your application requires the Call phone permission (which is required by default), application stores might not let users install your application on tablets.
For example:
- InterBase requires certain permissions:
- Internet: Allows applications to access network sockets. If you are building Client/Server apps accessing remote InterBase databases, this permission is a must-have. This permission is also required by InterBase "call home" silent license registration.
- Read external storage/Write external storage: Allows access to the external storage location where InterBase files, including your database files, are delivered. This permission is required for applications to perform read/write operations.
- Some FireMonkey components require certain permissions. For example:
- TCalendarEdit requires Read calendar and Write calendar permissions.
- TLocationSensor requires Access coarse location and Access fine location permissions.
Some Basic Android Permissions are Set for All FireMonkey Android Apps
New Android applications have the following required permissions set by default:
- Access coarse location
- Access fine location
- Call phone
- Camera
- Internet
- Read calendar
- Read external storage
- Write calendar
- Write external storage
- Read phone state
INTERNET Permission Is Always Set for the Development Configuration
Your Android apps have several Uses Permissions that are set by default, including the INTERNET permission.
- When you build an Android app with the Configuration set to Development (in the Project Manager), the INTERNET permission is always implicitly set, even if you disable the INTERNET permission on Uses Permissions. This is because the RAD Studio debugger requires the INTERNET permission.
- For the Application Store configuration, however, you can disable the INTERNET permission using Project > Options > Uses Permissions.
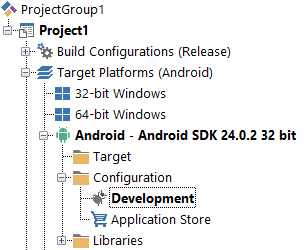
Here is the Project Manager with the Development configuration node set for an Android app:
Dialog Box Field Descriptions
| Options | Description |
|---|---|
|
Target, Apply, Save |
See Target Options. |
|
Common items |
Basic Uses Permissions
The following uses permissions can be used as required for most Android applications. Some of the most commonly used basic permissions are preset by RAD Studio when you create an Android app.
| Permission | Description |
|---|---|
|
Access coarse location |
Allows an app to access approximate location derived from network location sources such as cell towers and Wi-Fi. |
|
Access fine location |
Allows an app to access precise location from location sources such as GPS, cell towers, and Wi-Fi. |
|
Access location extra commands |
Allows an application to access extra location provider commands. |
|
Access mock location |
Allows an application to create mock location providers for testing. |
|
Access network state |
Allows applications to access information about networks. |
|
Access wifi state |
Allows applications to access information about Wi-Fi networks. |
|
Add voicemail |
Allows an application to add voicemails into the system. |
|
Authenticate accounts |
Allows an application to act as an AccountAuthenticator for the AccountManager. |
|
Battery stats |
Allows an application to collect battery statistics. |
|
Bind accessibility service |
Must be required by an AccessibilityService, to ensure that only the system can bind to it. |
|
Bind device admin |
Must be required by device administration receiver, to ensure that only the system can interact with it. |
|
Bind input method |
Must be required by an InputMethodService, to ensure that only the system can bind to it. |
|
Bind remoteviews |
Must be required by a RemoteViewsService, to ensure that only the system can bind to it. |
|
Bind text service |
Must be required by a TextService. |
|
Bind vpn service |
Must be required by an VpnService, to ensure that only the system can bind to it. |
|
Bind wallpaper |
Must be required by a WallpaperService, to ensure that only the system can bind to it. |
|
Bluetooth |
Allows applications to connect to paired Bluetooth devices. |
|
Bluetooth admin |
Allows applications to discover and pair Bluetooth devices. |
|
Broadcast sticky |
Allows an application to broadcast sticky intents. These are broadcasts whose data is held by the system after being finished, so that clients can quickly retrieve that data without having to wait for the next broadcast. |
|
Call phone |
Allows an application to initiate a phone call without going through the Dialer user interface for the user to confirm the call being placed. |
|
Camera |
Required to be able to access the camera device. |
|
Change configuration |
Allows an application to modify the current configuration, such as locale. |
|
Change network state |
Allows applications to change network connectivity state. |
|
Change wifi multicast state |
Allows applications to enter Wi-Fi Multicast mode. |
|
Change wifi state |
Allows applications to change Wi-Fi connectivity state. |
|
Clear app cache |
Allows an application to clear the caches of all installed applications on the device. |
|
Disable keyguard |
Allows applications to disable the keyguard. |
|
Expand status bar |
Allows an application to expand or collapse the status bar. |
|
Flashlight |
Allows access to the flashlight. |
|
Get accounts |
Allows access to the list of accounts in the Accounts Service. |
|
Get package size |
Allows an application to find out the space used by any package. |
|
Get tasks |
Allows an application to get information about the currently or recently running tasks. |
|
Global search |
Allows the global search system to access the data of specific content providers. Typically Global search is used when the provider has some permissions protecting it (which global search would not be expected to hold), and is added as a read-only permission to the path in the provider where global search queries are performed. The Global search permission cannot be held by regular applications; it is used by applications to protect themselves from all other applications except for global search. |
|
Internet |
Allows applications to open network sockets. |
|
Kill background processes |
Allows an application to call killBackgroundProcesses(String). |
|
Manage accounts |
Allows an application to manage the list of accounts in the AccountManager. |
|
Modify audio settings |
Allows an application to modify global audio settings. |
|
NFC |
Allows applications to perform I/O operations over NFC. |
|
Process outgoing calls |
Allows an application to monitor, modify, or abort outgoing calls. |
|
Read calendar |
Allows an application to read the user calendar data. |
|
Read call log |
Allows an application to read the user call log. |
|
Read contacts |
Allows an application to read the user contacts data. |
|
Read external storage |
Allows an application to read from external storage. |
|
Read history bookmarks |
Allows an application to read (but not write) the user browsing history and bookmarks. |
|
Read phone state |
Allows read only access to phone state. |
|
Read profile |
Allows an application to read the user personal profile data. |
|
Read SMS |
Allows an application to read SMS messages. |
|
Read social stream |
Allows an application to read from the user social stream. |
|
Read sync settings |
Allows applications to read the sync settings. |
|
Read sync stats |
Allows applications to read the sync stats. |
|
Read user dictionary |
Allows an application to read the user dictionary. |
|
Receive boot completed |
Allows an application to receive the ACTION_BOOT_COMPLETED that is broadcast after the system finishes booting. |
|
Receive MMS |
Allows an application to monitor incoming MMS messages, to record or perform processing on them. |
|
Receive SMS |
Allows an application to monitor incoming SMS messages, to record or perform processing on them. |
|
Receive WAP push |
Allows an application to monitor incoming WAP push messages. |
|
Record audio |
Allows an application to record audio. |
|
Reorder tasks |
Allows an application to change the Z-order of tasks. |
|
Send SMS |
Allows an application to send SMS messages. |
|
Set alarm |
Allows an application to broadcast an Intent to set an alarm for the user. |
|
Set time zone |
Allows applications to set the system time zone. |
|
Set wallpaper |
Allows applications to set the wallpaper. |
|
Set wallpaper hints |
Allows applications to set the wallpaper hints. |
|
Subscribed feeds read |
Allows an application to allow access the subscribed feeds ContentProvider. |
|
Subscribed feeds write |
Allows an application to allow write the subscribed feeds ContentProvider. |
|
System alert window |
Allows an application to open windows using the type TYPE_SYSTEM_ALERT, shown on top of all other applications. |
|
Use credentials |
Allows an application to request authtokens from the AccountManager. |
|
Use SIP |
Allows an application to use SIP service. |
|
Vending billing (In-app Billing) |
Allows using the In-app Billing service. See the Android documentation for additional information. |
|
Vibrate |
Allows access to the vibrator. |
|
Wake lock |
Allows using PowerManager WakeLocks to keep processor from sleeping or screen from dimming. |
|
Write calendar |
Allows an application to write (but not read) the user calendar data. |
|
Write call log |
Allows an application to write (but not read) the user contacts data. |
|
Write contacts |
Allows an application to write (but not read) the user contacts data. |
|
Write external storage |
Allows an application to write to external storage. |
|
Write history bookmarks |
Allows an application to write (but not read) the user browsing history and bookmarks. |
|
Write profile |
Allows an application to write (but not read) the user personal profile data. |
|
Write settings |
Allows an application to read or write the system settings. |
|
Write SMS |
Allows an application to write SMS messages. |
|
Write social stream |
Allows an application to write (but not read) the user social stream data. |
|
Write sync settings |
Allows applications to write the sync settings. |
|
Write user dictionary |
Allows an application to write to the user dictionary. |
- The documentation in the Description column of the table above is licensed under Apache 2.0. Copyright © Android Open Source Project.
Advanced Uses Permissions
The following uses permissions are only necessary for advanced Android features, and most applications should not need any of them.
| Items | Description |
|---|---|
|
Access checkin properties |
Allows read/write access to the "properties" table in the checkin database, to change values that get uploaded. |
|
Access surface flinger |
Allows an application to use SurfaceFlinger's low level features. |
|
Account manager |
Allows applications to call into AccountAuthenticators. |
|
Bind appwidget |
Allows an application to tell the AppWidget service which application can access AppWidget data. |
|
Brick |
Required to be able to disable the device (very dangerous!). |
|
Broadcast package removed |
Allows an application to broadcast a notification that an application package has been removed. |
|
Broadcast sms |
Allows an application to broadcast an SMS receipt notification. |
|
Broadcast WAP PUSH |
Allows an application to broadcast a WAP PUSH receipt notification. |
|
Call privileged |
Allows an application to call any phone number, including emergency numbers, without going through the Dialer user interface for the user to confirm the call being placed. |
|
Change component enabled state |
Allows an application to change whether an application component (other than its own) is enabled or not. |
|
Clear app user data |
Allows an application to clear user data. |
|
Control location updates |
Allows enabling/disabling location update notifications from the radio. Not for use by normal applications. |
|
Delete cache files |
Allows an application to delete cache files. |
|
Delete packages |
Allows an application to delete packages. |
|
Device power |
Allows low-level access to power management. |
|
Diagnostic |
Allows applications to RW to diagnostic resources. |
|
DUMP |
Allows an application to retrieve state dump information from system services. |
|
Factory test |
Run as a manufacturer test application, running as the root user. Only available when the device is running in manufacturer test mode. |
|
Force back |
Allows an application to force a BACK operation on whatever is the top activity. |
|
Hardware test |
Allows access to hardware peripherals. Intended only for hardware testing. |
|
Inject events |
Allows an application to inject user events (keys, touch, trackball) into the event stream and deliver them to ANY window. |
|
Install location provider |
Allows an application to install a location provider into the Location Manager. |
|
Install packages |
Allows an application to install packages. |
|
Internal system window |
Allows an application to open windows that are for use by parts of the system user interface. |
|
Manage application tokens |
Allows an application to manage (create, destroy, Z-order) application tokens in the window manager. This is only for use by the system. |
|
Master clear |
Allows you to call CheckinService.masterClear(), which resets the device settings to factory defaults and removes any user data. |
|
Modify phone state |
Allows modification of the telephony state - power on, mmi, etc. This is only for use by the system. |
|
Mount format filesystems |
Allows formatting file systems for removable storage. |
|
Mount unmount filesystems |
Allows mounting and unmounting file systems for removable storage. |
|
Read frame buffer |
Allows an application to take screen shots and more generally get access to the frame buffer data. |
|
Read logs |
Allows an application to read the low-level system log files. |
|
Reboot |
Required to be able to reboot the device. |
|
Set activity watcher |
Allows an application to watch and control how activities are started globally in the system. |
|
Set always finish |
Allows an application to control whether activities are immediately finished when put in the background. |
|
Set animation scale |
Modify the global animation scaling factor. |
|
Set debug app |
Configure an application for debugging. |
|
Set orientation |
Allows low-level access to setting the orientation (actually rotation) of the screen. |
|
Set pointer speed |
Allows low-level access to setting the pointer speed. |
|
Set process limit |
Allows an application to set the maximum number of (not needed) application processes that can be running. |
|
Set time |
Allows applications to set the system time. |
|
Signal persistent processes |
Allows an application to request that a signal be sent to all persistent processes. |
|
Status bar |
Allows an application to open, close, or disable the status bar and its icons. |
|
Update device stats |
Allows an application to update device statistics. |
|
Write apn settings |
Allows applications to write the apn settings. |
|
Write Google services |
Allows an application to modify the Google service map. |
|
Write secure settings |
Allows an application to read or write the secure system settings. |
- The documentation in the Description column of the table above is licensed under Apache 2.0. Copyright © Android Open Source Project.